Zero-knowledge Proofs on Bitcoin
A zero-knowledge proof enables a prover to validate the truth of a statement without disclosing any information about the underlying inputs. Among the various types of zero-knowledge proofs, zero-knowledge succinct non-interactive arguments of knowledge (zk-SNARKs) represent a significant advancement. These proofs are characterized by their non-interactive nature, compact proof sizes, and efficient verification times.
In recent years, the development of zero-knowledge proofs has led to the emergence of numerous ZKP systems. A particularly promising trend is the integration of ZKP with Bitcoin, which offers a scalable solution for the cryptocurrency. This document aims to introduce our ZKP solution, which leverages BitVM—a relatively mature paradigm in this domain. Our team is actively exploring the future potential of zk-SNARKs. As a member of the BitVM alliance, Bitlayer’s ZKP solution is intricately linked with BitVM. For more detailed information, readers are encouraged to refer to the bitvm website.
Groth16
In 2016, Jens Groth published a groundbreaking paper in which he formalized a proving system that significantly enhanced performance. Notably, for arithmetic circuits, the proofs generated consist of only two elements from the group and one element from the group . Here, and refer to two torsion groups within the context of pairing in Elliptic Curve Groups.
Due to its succinctness, the Groth16 proof has emerged as one of the most efficient and widely adopted solutions in the blockchain ecosystem, where resources on the main chain are extremely limited. Many Ethereum rollups prefer to utilize Groth16 for verification on Layer 1 (L1). Additionally, ZKVM projects such as Risc0 and SP1 incorporate Groth16 as the final recursive circuit. The Groth16 proof has been validated through numerous use cases, showcasing its robustness and versatility in practical applications.
How Groth16 is Applied to Bitcoin?
Like many other zk-SNARKs, Groth16 adheres to the same standard definition. It involves three algorithms, where is a public statement, is a witness, and a binary relation holds.
- : The setup procedure produces two public parameters and . Here, is a common reference string that defines the statement , while serves as a trapdoor for the relation .
- : The prover takes the common reference string and some and returns an argument for that relation.
- : The verifier either rejects (0) or accepts (1) the given argument . For the completeness of Groth16, this algorithm will return 1 if is satisfied.
One native way to scale Bitcoin is by proving off-chain and verifying on-chain. One of the main challenges with this approach is that the algorithm is too large to execute within a Bitcoin transaction. However, thanks to the optimistic computation paradigm of BitVM, the verification process can be split into manageable chunks, allowing the challenger to select one of these segments.
Despite this chunking method, the intermediate values of these segments need to be committed by the operator, which can still be substantial within the Bitcoin execution environment. Therefore, even with chunking, optimization of the algorithm is crucial for practical implementation.
This article will delve into the specifics of Groth16. First, some primary concepts and symbols will be quickly reviewed to align with the readers. Then, a key optimization related to verifying pairing will be introduced. Finally, the discussion will guide readers through the core idea of chunking the algorithm. By the end, readers will gain an in-depth understanding of zero-knowledge proofs in BitVM.
Elliptic Curve Group
The Elliptic Curve Group (ECG) is widely used due to its efficiency compared to finite fields under large primes. In this context, the BN254 elliptic curve group is selected for both security and efficiency. The BN254 curve is defined by the equation , based on a finite field , where is an efficiently chosen large prime.
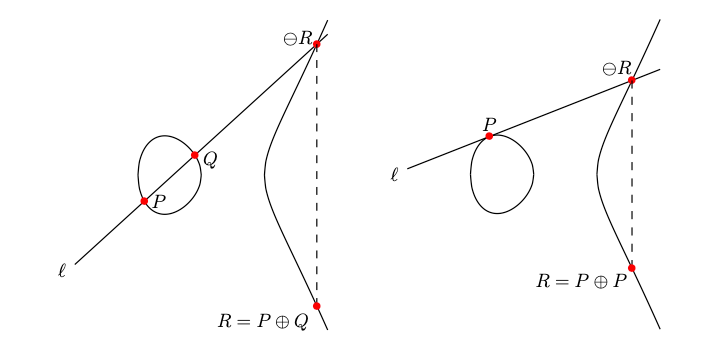
The ECG of BN254 is defined by divisors, and we introduce a point in projective space known as the point at infinity . The points on BN254, along with , form a group that adheres to the chord-and-tangent rule. The figure below illustrates two cases of the chord-and-tangent rule:
- , which represents the addition of two distinct points.
- , which represents the doubling of a single point.
- and , which demonstrate the rules governing the point at infinity.
Pairing Computation
Selecting an efficient pairing is a common method to reduce verification time. For the pairing in the BN254 elliptic curve group (ECG), two torsion groups are specifically chosen, both based on a smaller finite field with characteristic . Following the standard notation for pairings, we denote as , as , and as .
The ate pairing on -torsion groups is defined as a map
and is expressed as where , , is the embedding degree, and is a function whose divisor is . It is important to note that this is an optimized and reduced version. The computation of the Tate pairing in the BN254 ECG can be further simplified through algebraic optimization.
By choosing any such that , for , we have
which shows that is a valid substitution for . In the BN254 ECG setting, , where . The evaluation of is more efficient to compute by leveraging the Frobenius map. A similar technique is also applied during the verification of the pairing, rather than through direct computation.
Groth16 Verifier
The Groth16 verifier utilizes the properties of pairings while acknowledging its inherent inefficiencies. The proof is defined as
and the verifier accepts the proof if and only if the following condition holds:
where are precomputed during the setup phase, is the number of public inputs, and s are the public inputs.
This equation can be simplified to the following form, which outlines the two phases of the Groth16 verifier:
- Multiple scalar multiplications with fixed points.
- Four pairs of pairing computations, where three of them involve fixed points, and one does not.
The simplified equation is given by:
Optimization on Verifying Pairing
In the context of zk-SNARKs, the process of pairing computation provides us with an opportunity for pre-computation rather than direct pairing calculations. This article will present two main optimization strategies. We encourage readers to refer to the original ideas outlined in the paper On Proving Pairing, though it is important to note that this paper does not fully encompass the implementation details of BitVM.
The first optimization demonstrates that the final exponentiation of can be viewed as a reduction to the equivalence class of . If we can identify a pre-computed and verify that the result of the pairing is equal to , where is a multiple of that can be computed efficiently, this process will significantly enhance efficiency.
The second optimization indicates that the coefficients of each line in the Miller loop can be pre-computed. In the context of Groth16, the chord line and vertical line for the three fixed-point pairs are always constant. For the non-fixed-point pair, the chord line and vertical line can be verified at runtime.
Below, we outline the algorithm used by BitVM, which corrects errors found in the original paper. In the following description, represents all pre-computed lines that have been carefully selected for use. The index of pairs with non-fixed points is denoted by .